## Jfinal cms profile stored XSS
### Vulnerability Introduction
Jfinal cms, using the simple and powerful JFinal as the web framework, the template engine is beetl, the database uses mysql, front-end bootstrap, flat ui and other frameworks. Support multi-site, oauth2 authentication, account registration, password encryption, comments and replies, message prompts, website traffic statistics, article comments and pageview statistics, response management, rights management, etc.
### Vulnerability impact
- <= v4.7.1
### Vulnerability analysis
The vulnerability trigger point is in `com/jflyfox/modules/front/controller/PersonController.java`
```java
public void save() {
JSONObject json = new JSONObject();
json.put("status", 2);// 失败
SysUser user = (SysUser) getSessionUser();
int userid = user.getInt("userid");
SysUser model = getModel(SysUser.class);
if (userid != model.getInt("userid")) {
json.put("msg", "提交数据错误!");
renderJson(json.toJSONString());
return;
}
// 第三方用户不需要密码
if (user.getInt("usertype") != 4) {
String oldPassword = getPara("old_password");
String newPassword = getPara("new_password");
String newPassword2 = getPara("new_password2");
if (!user.getStr("password").equals(JFlyFoxUtils.passwordEncrypt(oldPassword))) {
json.put("msg", "密码错误!");
renderJson(json.toJSONString());
return;
}
if (StrUtils.isNotEmpty(newPassword) && !newPassword.equals(newPassword2)) {
json.put("msg", "两次新密码不一致!");
renderJson(json.toJSONString());
return;
} else if (StrUtils.isNotEmpty(newPassword)) { // 输入密码并且一直
model.set("password", JFlyFoxUtils.passwordEncrypt(newPassword));
}
}
if (StrUtils.isNotEmpty(model.getStr("email")) && model.getStr("email").indexOf("@") < 0) {
json.put("msg", "email格式错误!");
renderJson(json.toJSONString());
return;
}
model.update();
UserCache.init(); // 设置缓存
SysUser newUser = SysUser.dao.findById(userid);
setSessionUser(newUser); // 设置session
json.put("status", 1);// 成功
renderJson(json.toJSONString());
}
```
The user modifies the data, the incoming data is not filtered, stored directly in the database, and finally rendered to the front end, resulting in a storage XSS.
### Vulnerability recurrence
1. Register a regular user.
2. Modify the information
3. Fill in the xxs payload in the user nickname.
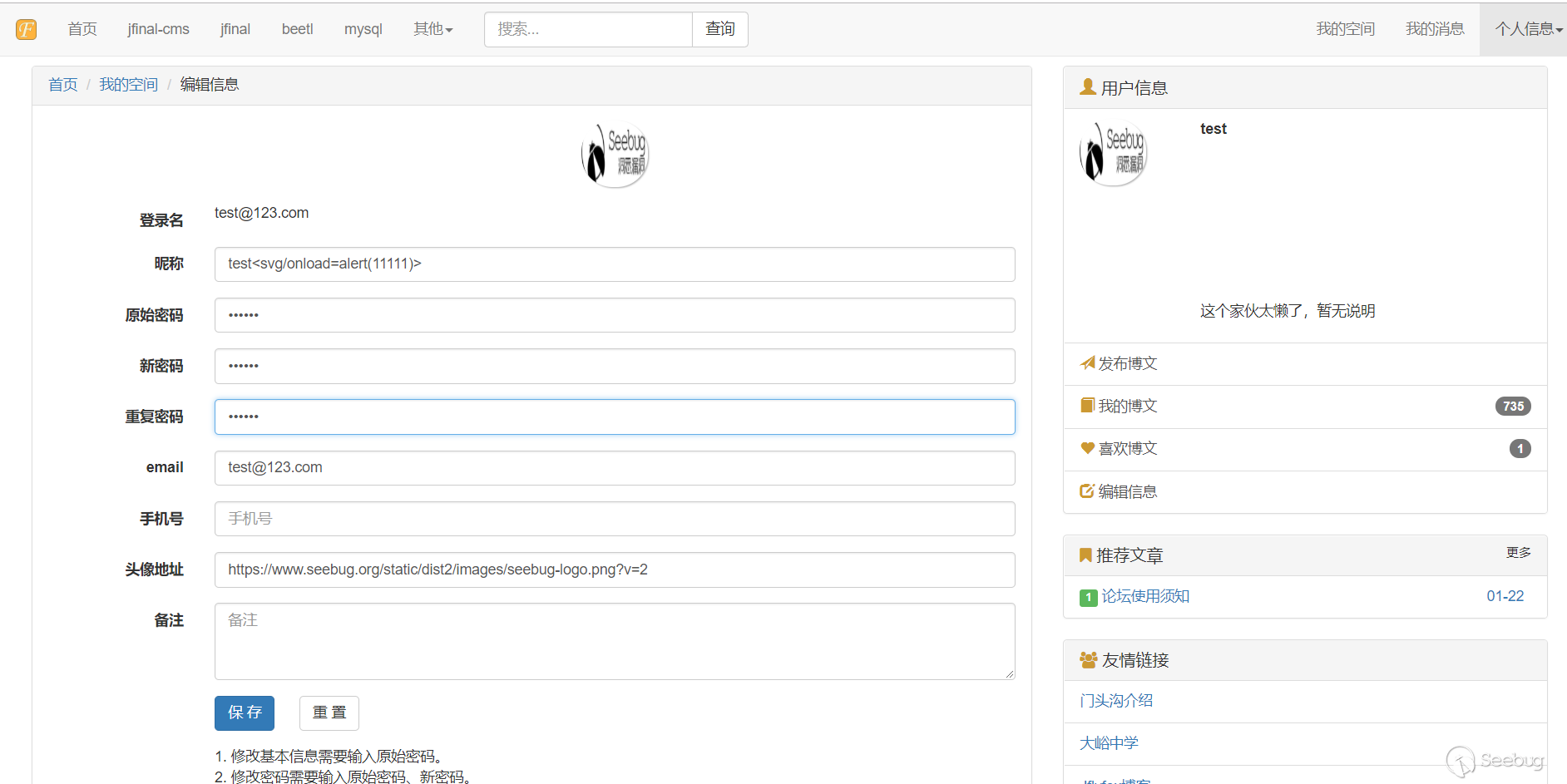
4. Click Save
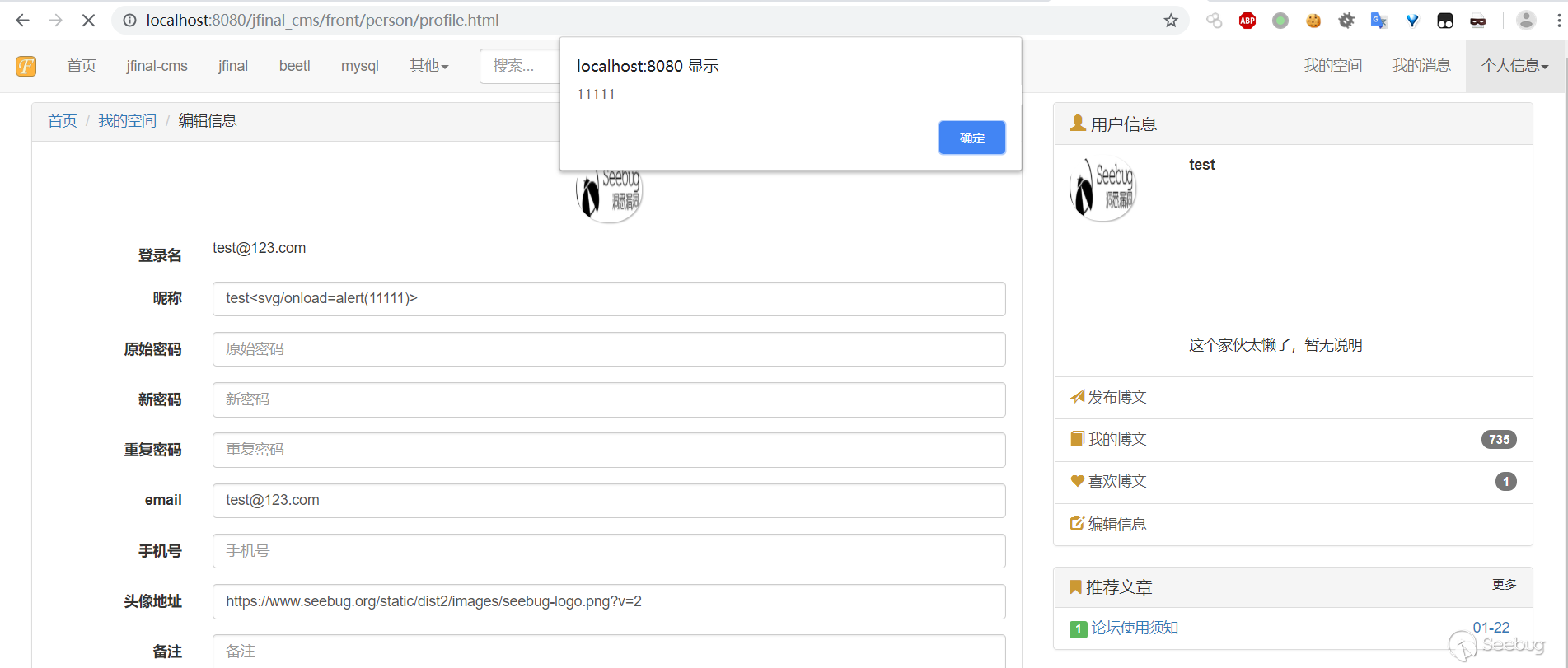
5. Viewing the user profile will trigger the payload, and XSS will be triggered when the user's nickname is viewed in the background.


暂无评论