## Jfinal cms background arbitrary file read
### Introduction to Vulnerability
Jfinal cms, using the simple and powerful JFinal as the web framework, the template engine is beetl, the database uses mysql, front-end bootstrap, flat ui and other frameworks. Support multi-site, oauth2 authentication, account registration, password encryption, comments and replies, message prompts, website traffic statistics, article comments and pageview statistics, response management, rights management, etc. Its background management department can modify the template path to cause arbitrary file read vulnerabilities.
### Vulnerability Impact
- <= v4.7.1
### Vulnerability Analysis
The vulnerability trigger point is in `com/jflyfox/modules/admin/folder/FolderController.java`
```java
Public void save() {
Integer pid = getParaToInt();
TbFolder model = getModel(TbFolder.class);
// log added
Integer userid = getSessionUser().getUserid();
String now = getNow();
Model.put("update_id", userid);
Model.put("update_time", now);
If (pid != null && pid > 0) { // update
Model.update();
} else { // add
// Site settings
model.setSiteId(getSessionUser().getBackSiteId());
Model.remove("id");
Model.put("create_id", userid);
Model.put("create_time", now);
Model.save();
}
// update the directory cache
New FolderService().updateCache();
renderMessage("save success");
}
```
When the user modifies the template path, the incoming data is not filtered. When the engine is rendered in the foreground, the template directory is not restricted, resulting in arbitrary file read vulnerabilities.
### Vulnerability recurrence
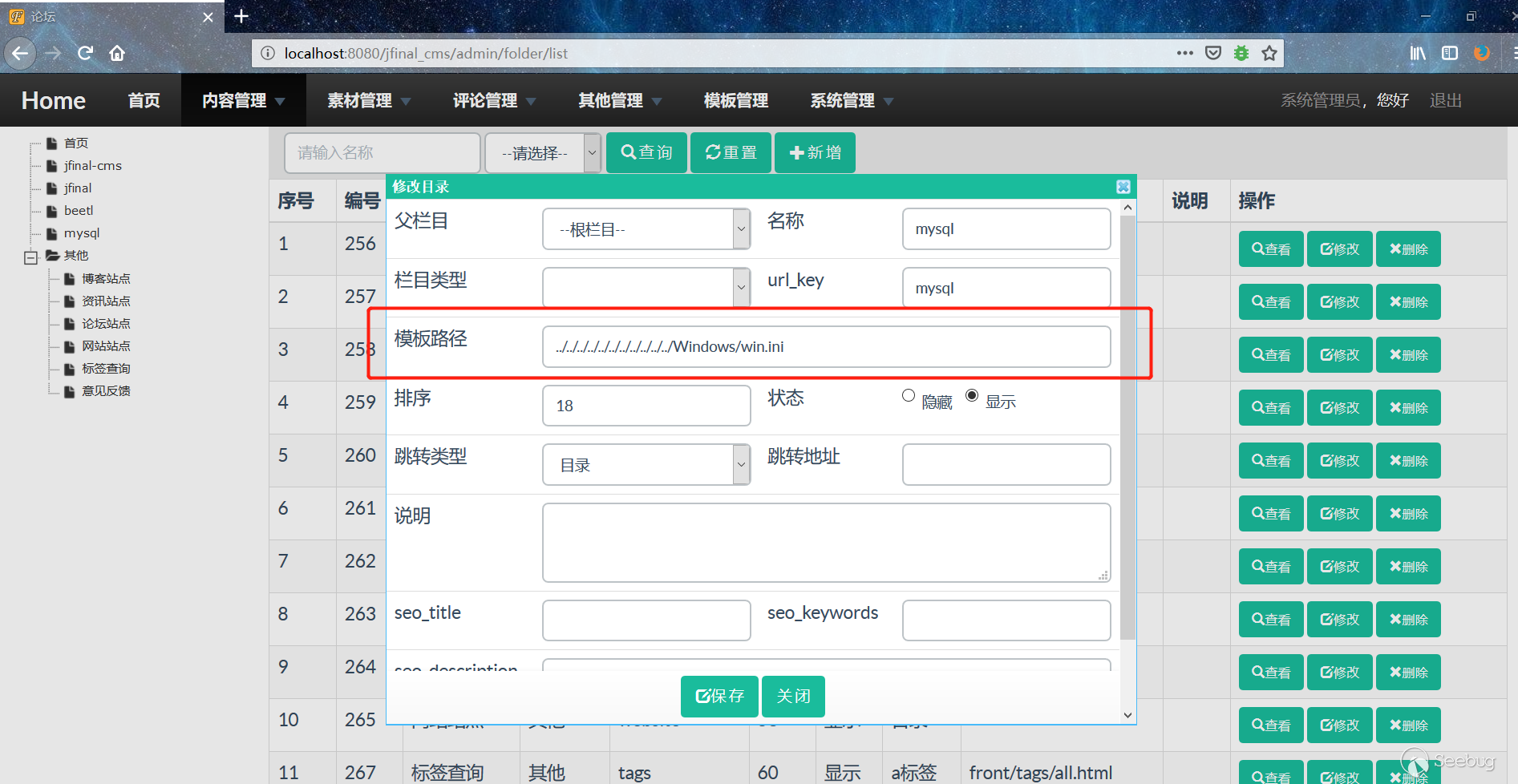
1. Login to the background
2. Click Content Management - Column Management, modify the template path, and save.
Http://localhost:8080/jfinal_cms/admin/folder/list
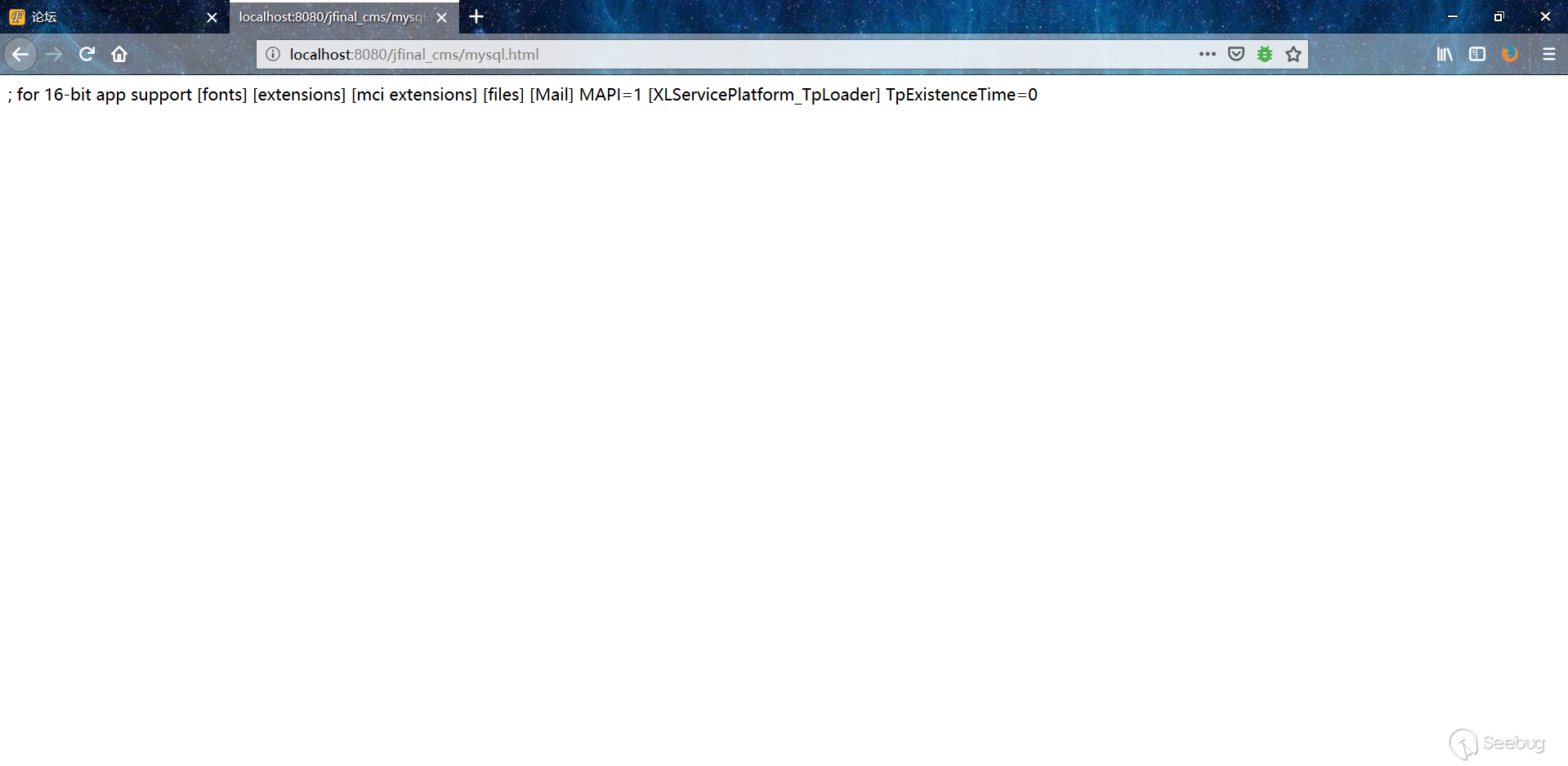
3. The front desk accesses this section.


暂无评论